How to use Artificial Intelligence in Marketing
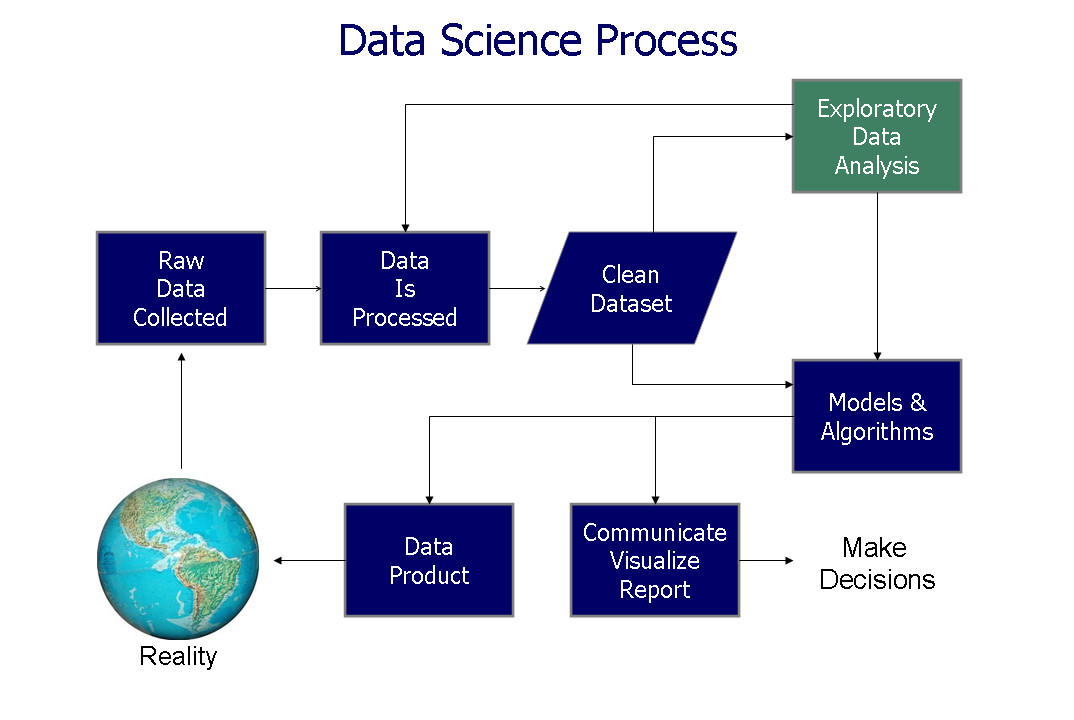
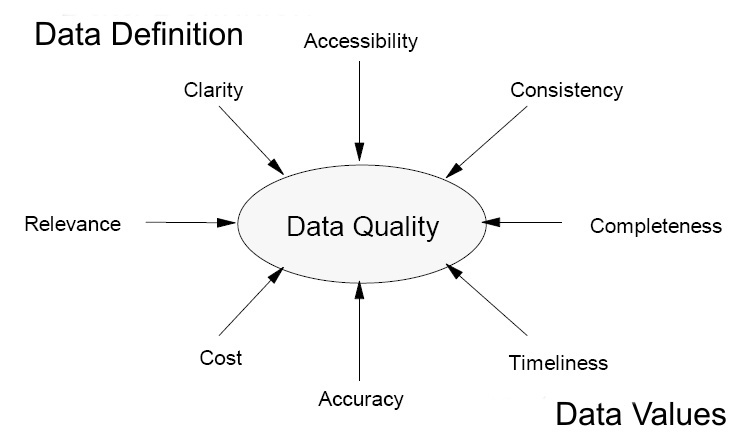
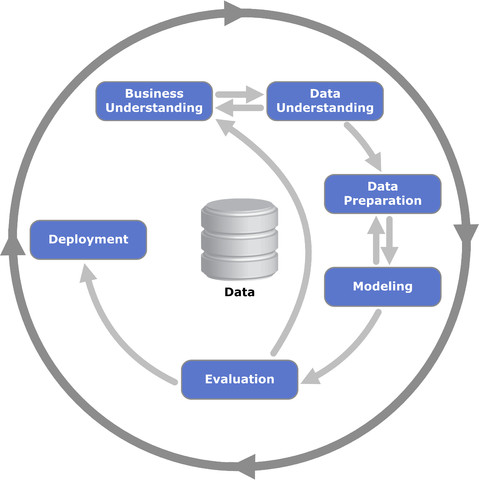
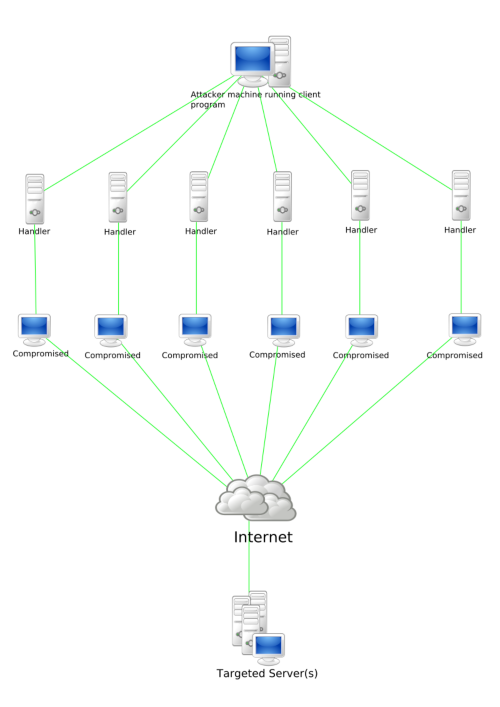
5 Top Ways to use Artificial Intelligence in Marketing Click for full size Infographic You can use the power of artificial intelligence and machine learning to dramatically improve the abilities of your marketing department, and create an impact that promotes engagement and meaningful customer relationships. Optimize Product Pricing with Dynamic Pricing - Optimizing product prices helps to minimize cannibalization while maximizing revenues. Acquire New Customers - You can leverage biometrics and data from sensors to better understand how your content impacts your audience.